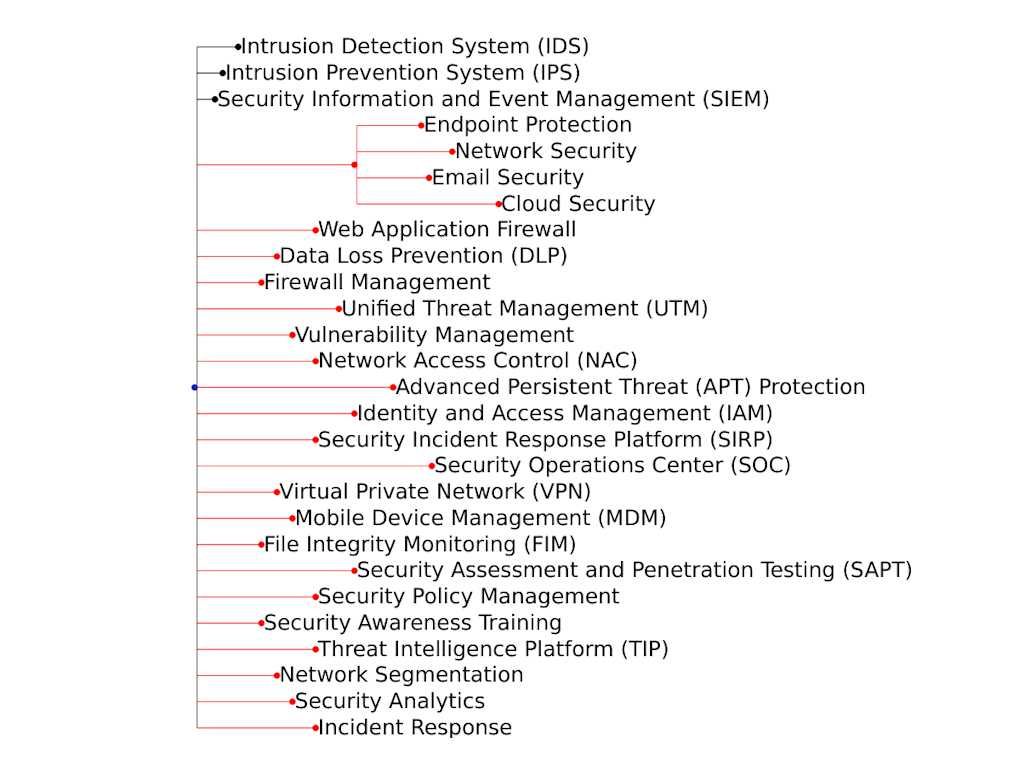
Risk Model based upon a simple Security Survey.
With the length and colour of the lines indicating a higher risk for these dependencies.
This was built using the ete4 library.
etetoolkit.org
For my academic project, I decided to conduct research into Dependency Modelling and Risk-Resillience. With my aim being to dissect the problem of scale of dependencies within large organisations.
I first sought to replicate simple Dependency Modelling techniques, by presenting dependencies in the Parent-Child relationship. This was so I can implement a control to compare different modelling techniques to.

Risk Model based upon a simple Security Survey.
With the length and colour of the lines indicating a higher risk for these dependencies.
This was built using the ete4 library.
etetoolkit.org
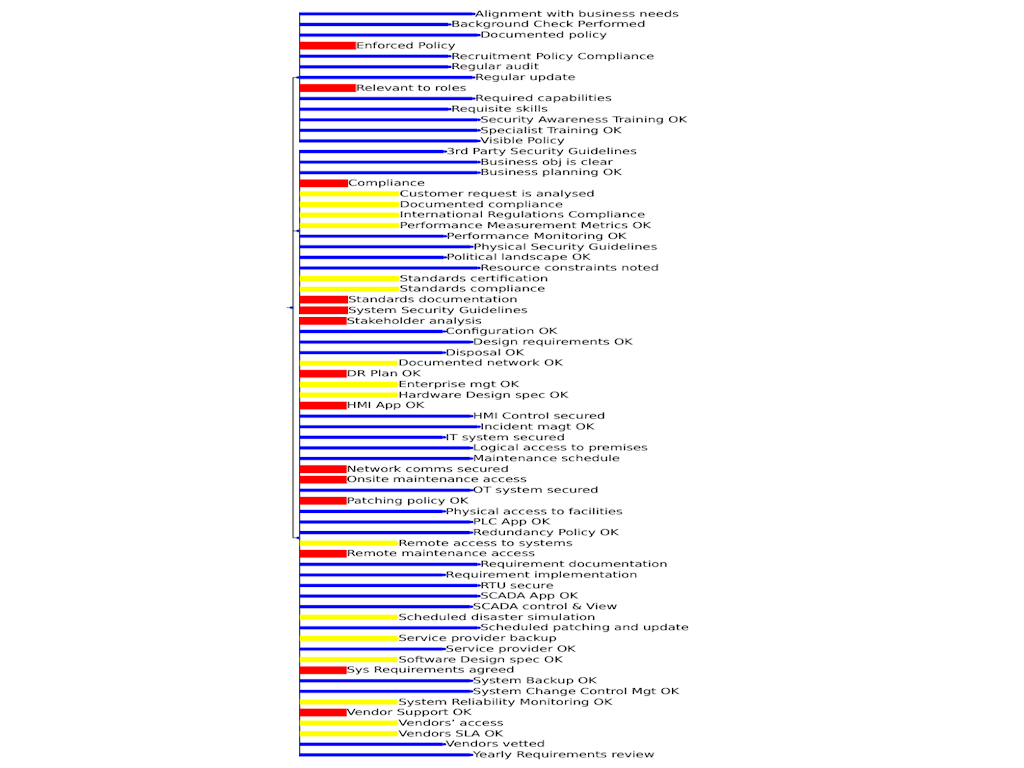
An advanced version of the previous Model which now calculates total risk to each of the System's Dependencies.
Blue - Low Risk, Yellow - Medium Risk, Red - High Risk
(Length of lines in proportion of Risk and for Clarity).
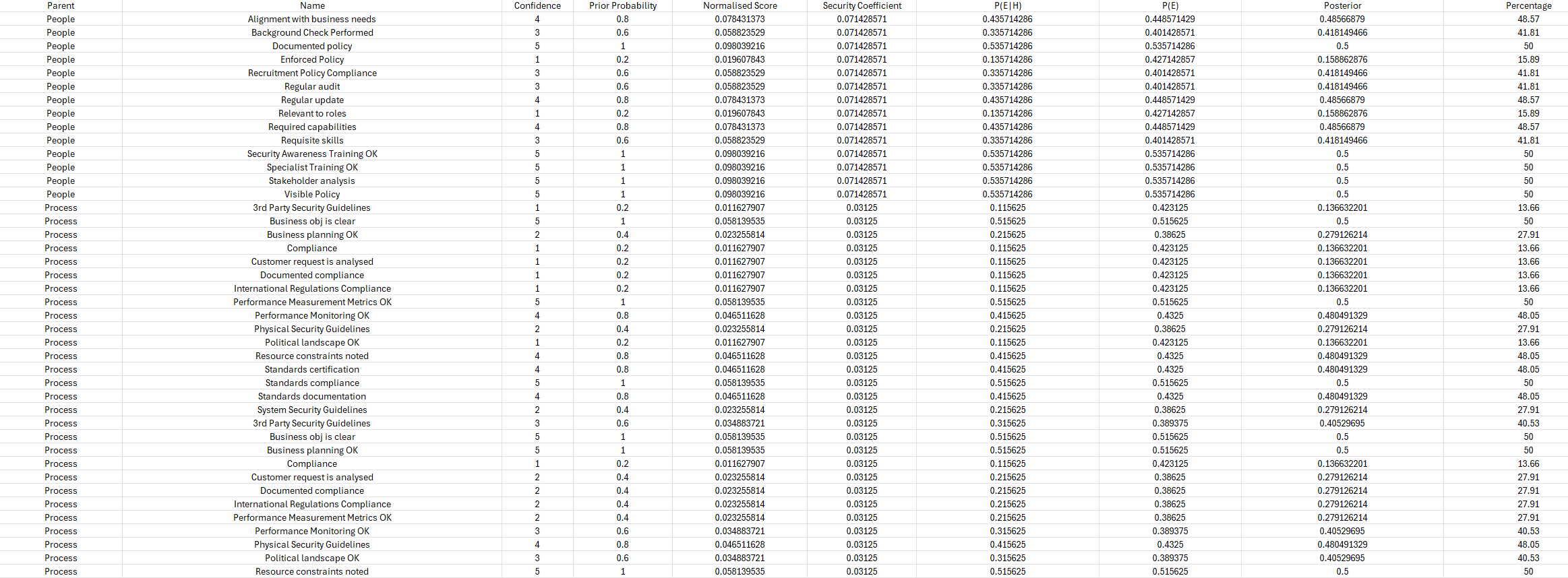
This is the Security Survey which is implemented in Excel.
It takes in confidence scores for each of these categories and normalises them into giving a Bayesian Probability of Risk.
(Extended Dependency Modelling Technique for Cyber Risk Identification in ICS - Rotibi et al.)
| System | Function | Example in Information Security |
|---|---|---|
| 1 | Operations | Firewall, Intrusion Detection System (IDS) |
| 2 | Coordination | Incident Response Team (IRT), Security Incident Management |
| 3 | Control | Security Policy Enforcement, Access Control Systems |
| 4 | Intelligence | Threat Intelligence Platforms, Vulnerability Scanning |
| 5 | Policy | Governance, Risk, and Compliance (GRC) Framework |